The growth of International networks, public and private email systems, and radio communication requires a greater need for security. Protocol analysts can view data streams on the network, and by design the Internet allows wiretapping. It is estimated that 20% of the message traffic sent via the Internet is copied and stored somewhere by someone (other than the sender or intended recipient). On the Internet, anybody (apart from the recipients) just look and duplicate your mail or change the content of the messages.
Apart from insecurity of data, as is being transmitted, there are also security issues regarding data legitimately stored in servers. Hackers can break into the server to:
And to secure Internet data handling requires:
These requirements are realised through a number of security measures - both software-based and hardware-based. In the TCP/IP set up, the measures cover the whole model structure, from the physical layer through the application layer. Here is a summary of some of the measures.
2.4.1 Cryptographic
A technique which provides a way to transmit information across an untrusted communication system (e.g. Internet) without disclosing the content of the information to anybody monitoring the line. One encryption method uses a pair of keys. The sender uses the public key to encrypt the message and the receiver uses a private key to decrypt/decipher the message. The longer the key (in bits) the more secure it is. Presently, the 128-bit scheme is the market leader. The public/private key scheme is further supplemented by a digital signature scheme, which authenticates the sender.
2.4.2 Firewall
A firewall is a computer (server) that connects a trusted network with an untrusted network such as the Internet. It prevents some external users from accessing the internal LAN and also can restrict internal users form accessing the Internet. The restricting variables are:
The basic and main function of firewalls is to filter information. A firewall examines all data packets and then takes appropriate action - to allow or not to allow. Implementations of firewalls include:
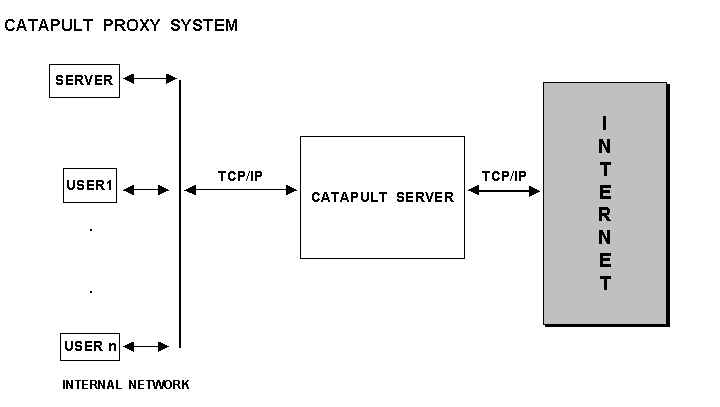
2.4.2.1 Proxy Servers
This runs on a firewall host as a store-and-forward system. It takes FTP, HTTP, TELNET, etc., requests from Internal and external users, examines them and then takes appropriate action. A proxy server can have additional functions. One very good example of a proxy server is Microsoft’s "Catapult " proxy server; which is capable of:

The catapult server makes it possible to securely use the Internet as an alternative to use private dedicated telephone connections
2.4.2.2 Routers
Commercial Routers can be programmed to hold predefined lists of addresses, and; packet filtering is done based on the list. Some routers may be sophisticated enough to give proxy-like services.
2.4.3 Physical Isolation
This security measure requires more than one internal LAN. The servers are isolated from internal network and users can access the Internet through a separate firewall. The other LAN has dual communication with the Internet.
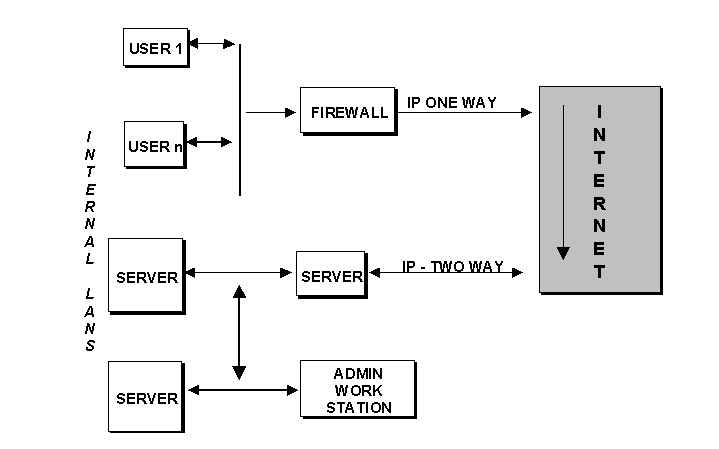
Note: To access the server on the 2-way LAN users on the internal LAN, it has to "backtrack" over the Internet connection. The administration of the servers is done via the Admin Workstation. This is a limitation of the system.
2.4.4 Protocol Isolation
On the server computer two different Network Interface Cards (NICs) are used; one connected to the internal network and using IPX and, the other card connected to Internet and running TCP/IP protocol. There is no across network traffic because each network is using a different protocol but both internal users, and users from the Internet can share information from the server each one of them is using a different protocol.

2.4.5 Protocol Isolation with Server Replication
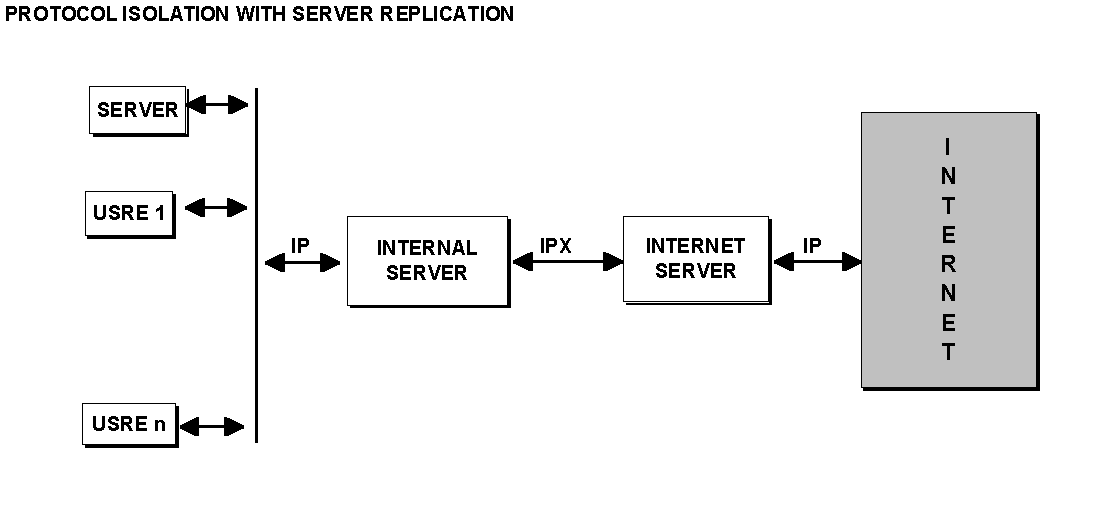
This is a variation of (d) above with dual servers between which data is replicated. Protocol isolation is achieved by running IPX between the two servers, which individually each one of them runs TCP/IP. Because ALL information is replicated between the two servers both Internet users and internal users have access to the same and complete set of data.
2.4.6 Multi-Homed System with Routing Disabled
In this scheme there are two NICs in use, each is attached to a different network. Although both of them runs TCP/IP and since routing is DISABLED there can not be any traffic across networks, hence, the security of the system. It is the routing disabling which is the key to the security of the system.

2.4.7 Tunnelling Through the Internet
This is a software solution in which the TCP/IP software encrypts data before sending it over the network. IP tunnelling ensures secure, private communication for online activities like connecting to the office via the Internet. Note: Client/Server tunnelling software must be appropriately installed.