Presently meteorological data/products can be communicated between centres using the GTS or the Internet.
2.1 Networking
A network is a collection of computers and other devices along with cabling and the network interface controllers that are inside the computer and the software.
The principal aim of networking is to have a sharing of data and information resources. The WMO GTS has the same main function of ensuring global sharing of meteorological data and information. The Internet is also a data/information sharing system. It seems natural therefore to briefly discuss networking before discussing the GTS and the global network of networks (Internet), and how the GTS can interact with Internet and benefit from its technology.
List of some network hardware and peripherals:
Two principal types network software:
a. Network Operating Systems (NOS)
b. Network Applications (2 types)
2.1.1 The OSI Model
If every network vendor were to build a network in ones own way, the situation would be extremely complicated and chaotic. The International Standard Organisation (ISO) proposed a model in which network communication is divided into seven (7) layers. The model is called, The Open System Interconnection (OSI), which provides a framework and guidelines for network communication. The philosophy of "divide and conquer " is used in this system, the complicated system is divided into smaller manageable layers. There are set of rules that has to be followed to implement any of the layers, called PROTOCOL specifications. The rules are like house drawings, which, if given to different contractors will result into similar but not identical houses. The drawings are the protocols and the houses are implementation of the protocols. The functions of the layers are summarized in Annex 8.
The 7 layers of OSI model are sometimes grouped into 3 broad categories based on broad functionality or services they offer, these are:
2.1.1.1 Connection Services (Layers 1 – 2)
This group is concerned on how information gets from one computer in to the network connection medium (e.g. cable) and how the information moves from the medium into the computer at the other end. The implementation rules (protocols) for these two layers have to consider:
There are number of set of protocols in which vendors can adhere to when designing the connection services such as, the IEEE (Institute of Electrical and Electronic Engineers) suite, Ethernet, Token Ring, ARCNET, etc. To have a good understanding of these sets of protocols, it requires some basic knowledge on the four considerations upon which the rules are based:
a. Medium Types (Types of transmission media)
Data can be transmitted using either bound or unbound medium.
There are many in determining which medium implementation should be used. In a Local Area Network (LAN) cabling would be used but to connect two LANs which are far apart, microwave could be chosen. There are different accessories required to build network and interconnect them, e.g. hubs, repeaters, connectors, terminal plugs, modems, routers, etc., which all go into preparing the road on which data will travel.
b. Transmission Data Rates (Data transmission rates in the media)
How much data can be transmitted:
It could be as little as a few thousand bits per second or as much as hundreds of millions of bits per second. In the Internet situation the "last longest mile" phenomenon is the most speed restricting factor to end users. It should also be remembered that graphic files are generally huge that requires high data transmission speed.
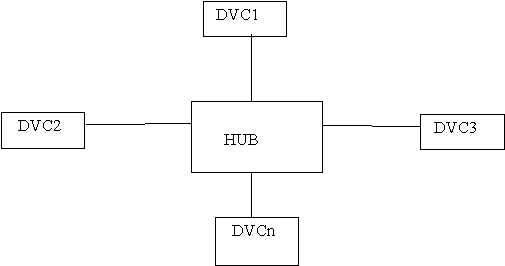
c. Network Topologies (The physical layout of the media and devices)
Describes the physical layout of the network medium and attached devices. (DVC=Device)

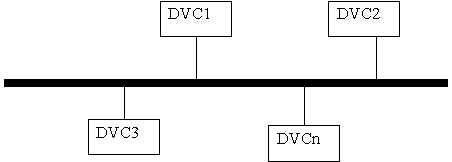
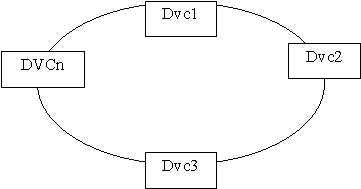
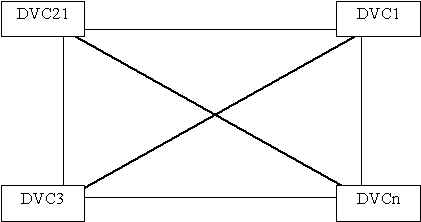
d. Access Methods (Methods to access various media)
Access methods are the rules that govern how the various devices that make up the network communicates, either using a common medium or on point-to-point links.
CSMA/CD stands for Carrier Sense, Multiple Access with Collision Detection. This is an access method in which any device wishing to transmit data/products listen to the medium, when it is idle the device transmits. If more then one device transmits at the same time the data packets will collide to produce noise detectable by ALL network devices. Transmission will terminate and the transmitting devices will choose a RANDOM time interval to re-schedule retransmission of the collided frame.
In this access method, the devices do not share a common medium but instead have a point-to-point link which form a closed loop (ring). A special bit pattern called the TOKEN is generated and circulates on the ring and a device can only transmit if it has the token.
In this system one computer designated as controller will poll the others to find out whether they have something to transmit.
Each of these access methods has their own advantages and disadvantages. Ethernet and Token Ring are very popular. Ethernet is the most common for small networks because it is cheaper.
There are many connection services protocols. The three most common protocols that many vendors use to implement the connection services (Physical and Data Link layers) of the OSI Model are:
The Institute of Electrical and Electronic Engineers (IEEE) developed the so called "802 Series" protocol suite which deals with the Physical and Data Link layers. The 802 series has several components, 802.2 through 802.5.
- All attached devices operate independently (peer to peer)
- All devices are attached to a shared medium (bus)
- Medium access control is by CSMA/CD
- Various kinds of Coaxial cables are used
Ethernet is considered simple, fairly robust, inexpensive and is therefore the most popular. Ethernet resembles the IEEE 802,3 standard in many ways.
2.1.1.2 Transport Services: Layers 3 – 6
These services augment the connection services to provide reliable communications between computers. The services ensures that:
The most popular protocols to operate within the Transport Services are the TCP and IP.
The Origin of TCP/IP
The US government funded the development of suite protocols which collectively has come to be known as the INTERNET Protocol, essentially to enable the networking of dissimilar computer systems the government had. The two best known components of the Internet Protocol suite are the IP and TCP. TCP fulfilling the functionality of the OSI Transport Layer and IP fulfilling the functionality of the OSI Network Layer.
The TCP/IP Implementation
Various vendors have used the ISO OSI model to produce various networks: NetWare, SNA Network, DECnet, AppleTalk, TCP/IP, etc. Annex 8 to this report shows the "NetWare" and "TCP/IP" implementation of the model. The WMO GTS had decided to use TCP/IP for a number of reasons, not least because Internet also uses it. There is more to TCP/IP than just TCP and IP. TCP/IP is a SUITE containing many different protocols that work together. Brief description of the two most popular components of the suite.
This protocol takes care the packaging of data for delivery. It defines an address scheme that UNIQUIELY identify devices on private networks and on the Global Internet (IP address). The data packets contain IP addresses of the sender and the recipient. The ROUTERS determine exactly what to do with the packet used in this information.
Error checking and sequence numbering of the data packets are two main functions of TCP, telling the sending device to retransmit any lost or erroneous data packets.
Annex 8 shows the TCP/IP OSI model implementation has the top four layers bundled together so that, for example, the File Transfer Protocol (FTP) carries out all the functions of the OSI model layers 5 to 7.
2.1.1.3 Application Services: Layer 7
Services in this layer depend on the other two services. The Application Services let an application on one computer talk to a similar application on the other computer in order to perform functions like copying files, etc.
2.1.2 Network Classifications
Networks can be classified either by the area they span or by the way the resources are distributed on the PCs that are connected on the network.
2.1.2.1 Geographical Area Coverage
These networks are based on the size of the geographical area they span:
a. Local Area Network (LAN)
This network spans one office or one floor of a building or the whole building, or could even several neighbouring buildings. LANs have high data transfer, low error rates and inexpensive media.
b. Wide Area Network (WAN)
Normally, WAN is the result of interconnecting several LANs across different cities or countries, e.g. Internet. Communication over WAN takes place via telephone lines, satellites or terrestrial microwave systems.
2.1.2.2 Resources Distribution
Networks can also be classified based on the way resources are distributed. Resources may be located on each of the computers that are on the network (peer to peer architecture), or may be placed on a few specific computers called "Servers". Other computers called "Clients", would access the resources stored in the servers (client/server architecture).
a. Peer-to-Peer Architecture
In this architecture, computers on the network may share its resources with others. All computers are "peers" (are equal) and there is no centralised resource management. While this architecture may work well for small networks, the lack of central resource control complicates resource access for networks with a large number of users.
b. Client/Server Architecture
In this architecture, the resources are placed on the server where all users can obtain them. There are e-mail servers, file servers, print servers, web servers, etc. The management of the resources (servers) is centralised and carried out by one computer - Network Server. Depending on the volume of the resources, more then one resources can be co-located on one physical computer; e.g. one PC can store e-mail and file resources.
Notes: